Ready to experience the future of cybersecurity? Request a personalized demo of our 360 AI – Cybersecurity Platform and see how intelligent protection meets operational excellence.
Once you submit your request,a member of our technical team will reach out to you promptlyto schedule your demo.
We’ll guide you through the entire process—from understanding your security needs to showcasing how our platform adapts to your environment. Expect a seamless, insightful walkthrough tailored to your organization’s goals.
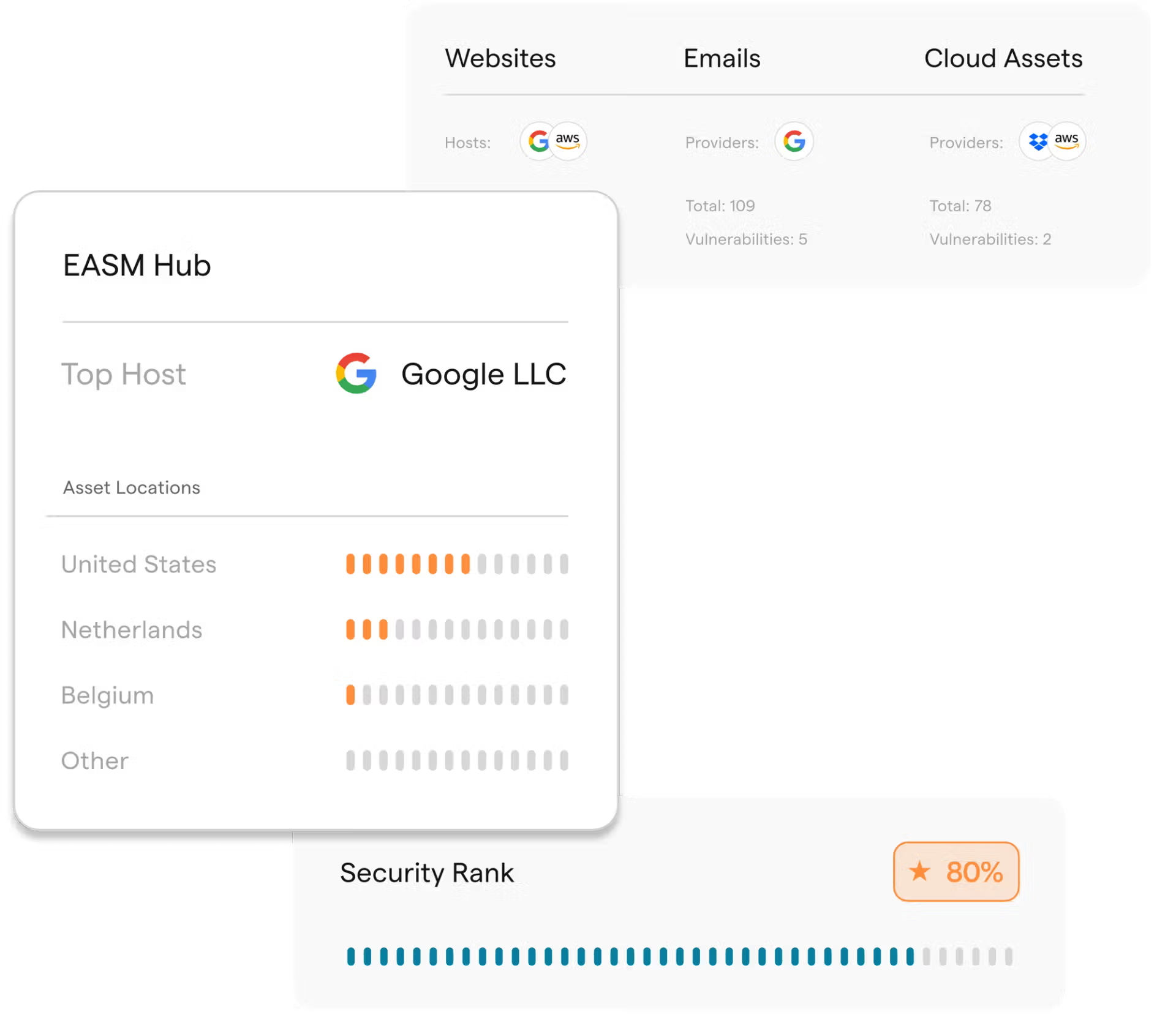
EASM Hub
Provides threat intelligence, dark net monitoring, and vulnerability management.

Secure Your External Digital Assets with Rotate EASM Hub
External Attack Surface Management (EASM) with advanced threat intelligence, vulnerability monitoring, and darknet data leak scanning to protect your organization’s public-facing assets.
Strong cybersecurity requires constant
vigilance against lurking and
opportunistic threats. The EASM Hub
keeps your guard up constantly, giving
you visibility across your attack surface
and high-precision intelligence.
Don’t Let Attackers See Vulnerabilities You Don’t
- Continuous Monitoring and Visibility: The EASM Hub continuously scans the internet to identify and maintain a dynamic list of your organization’s public assets, including domains, IPs, ports, and certificates. Safeguard your digital perimeter with real-time monitoring and actionable insights.
- Vulnerability Detection and Prioritization: Stay ahead of potential threats with proactive monitoring that alerts you to vulnerabilities in real time and shows you which assets are the most likely targets for cybercrime.
- Actionable Insights and Remediation with Rotate AI: Use data-driven analytics to prioritize remediation efforts and strengthen your defenses against cyberattacks. You can depend on live support and Rotate AI to help you understand vulnerabilities and deliver step-by-step guidance to resolve every issue.
- Centralized External Attack Surface Management: Gain an unified view of all vulnerabilities and issues from one comprehensive dashboard. Streamline operations and enhance efficiency by managing risks across your entire external attack surface, to ensure the most critical issues are prioritized.



